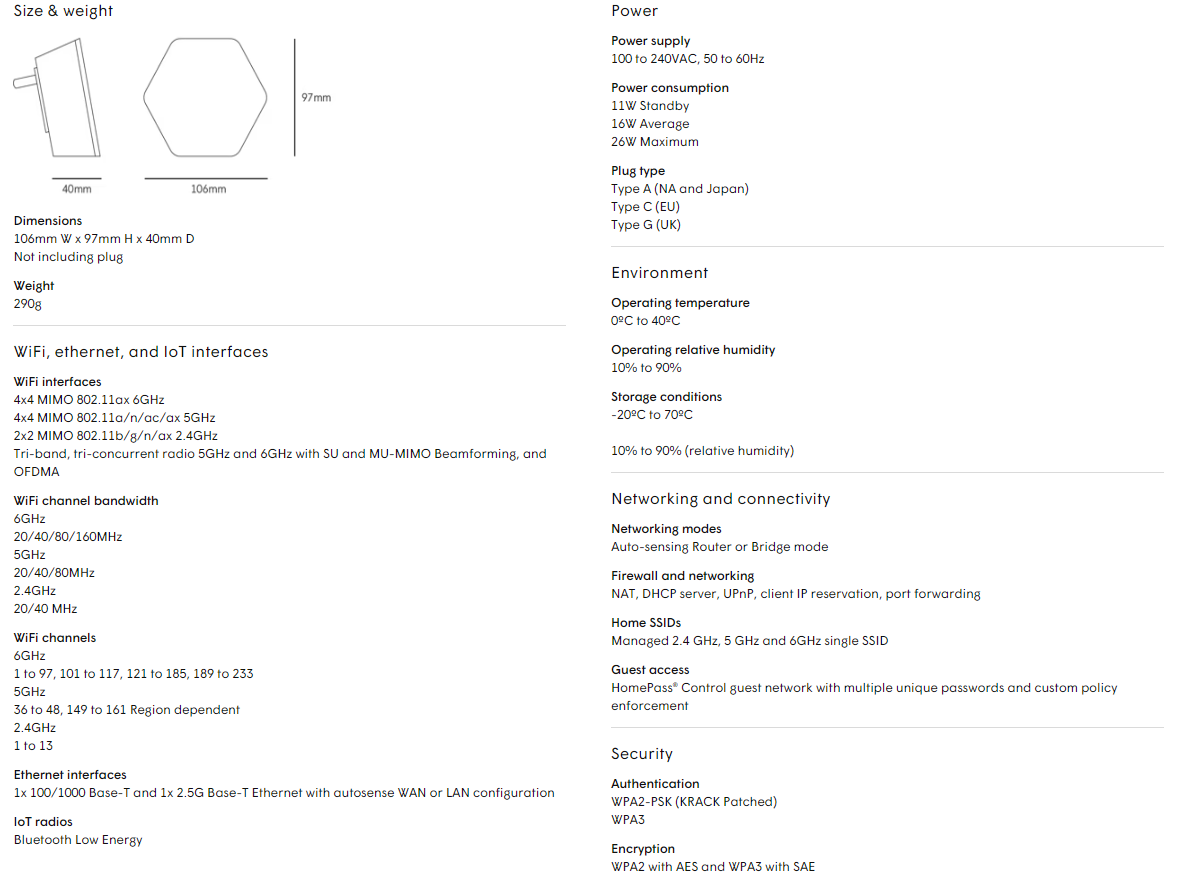
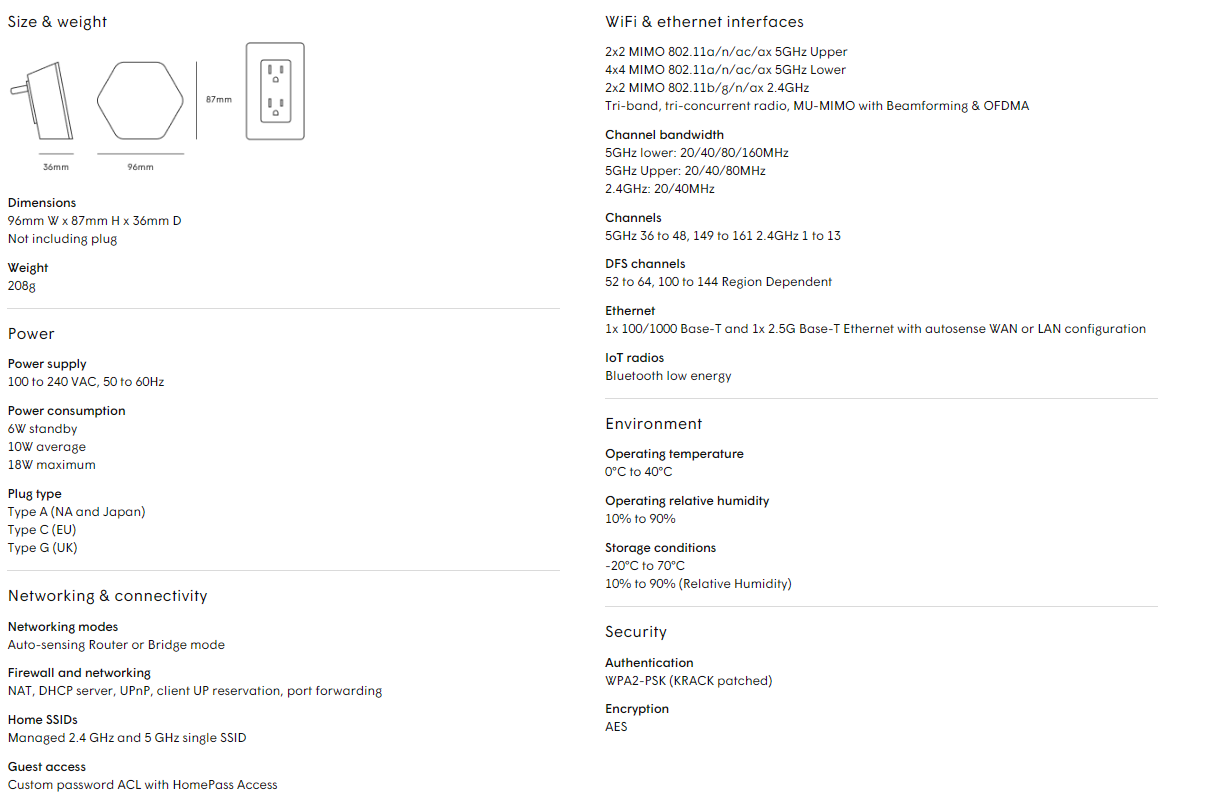
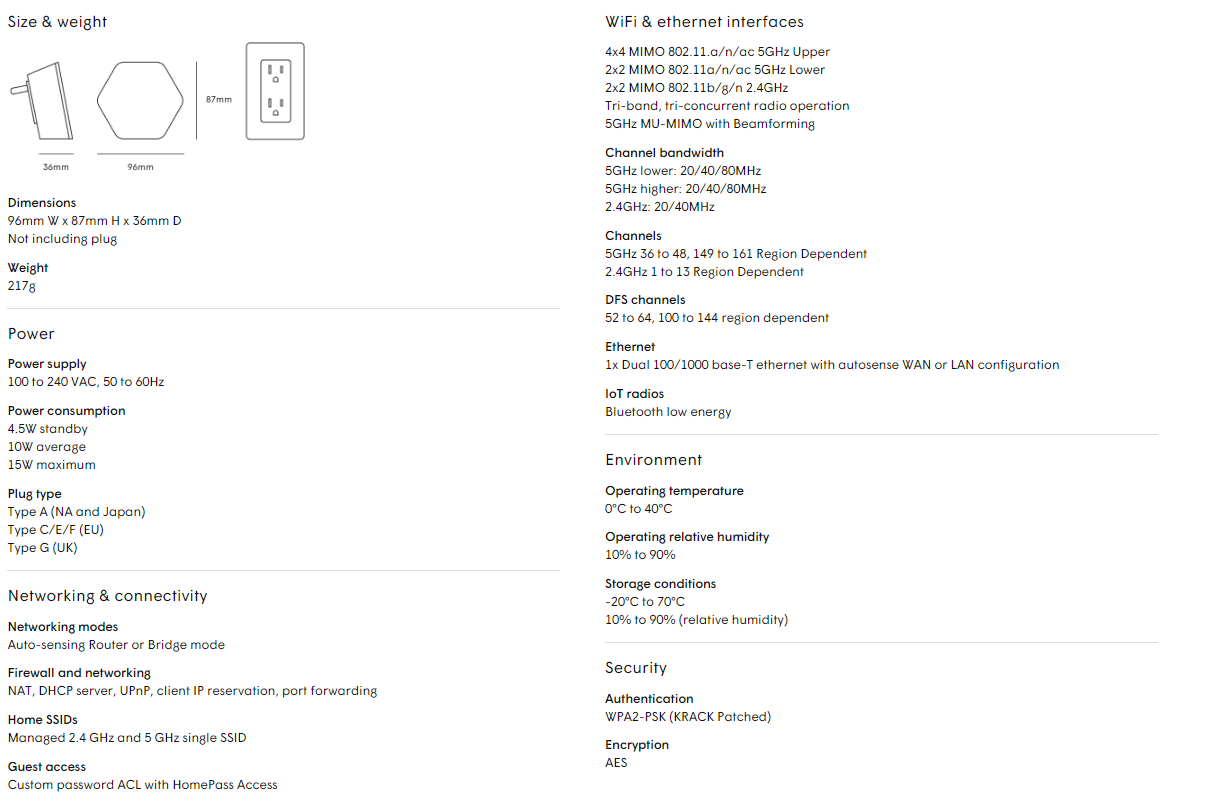
Schedule a Free Network Security Consultation
Get our FREE eBook, Ransomware for Dummies from our partner, Cisco.
When large, well-known companies experience data breaches, small and medium businesses (SMBs) may not heed the warning, thinking that hackers have bigger fish to fry and won’t target them. However, no type or size of company gets overlooked by cyber criminals.
The IT security news outlet Help Net Security reported that nearly half of SMBs have been targeted by ransomware and almost three-quarters of these victims have paid a ransom. Hackers are looking to steal and compromise sensitive and personally identifiable data, no matter what the source.
Now is the time for SMBs to assess and strengthen their security posture. Examining a select group of security areas will give your company a place to start while making the most impact.
Here’s an overview of 5 key areas to focus on when developing a winning security strategy for your business:
1) Software
Software is a key area of vulnerability for SMBs. If your company isn’t staying up to date with patches and upgrades, hackers can exploit issues with applications and operating systems to infiltrate your network and stage attacks on your entire system.
Your company should reboot equipment regularly to install updates. Software should also undergo regular anti-malware scans and backups to prevent the data it uses from being lost or stolen.
2) Mobile Devices
With employees increasingly using mobile devices for work, including their own smartphones and tablets, your company must have processes in place for securing and tracking these devices. Our research predicted that in the next 3 years, 90% of IT organizations will be supporting business applications on personal mobile devices.
A mobile device that contains company and customer information should be locked when not in use. Employees that rely on mobile devices for work should have proper security tools installed to allow them to connect to the company network safely. Your company must also have control over which devices can access your network. Endpoint visibility can ensure a device meets your security criteria before it gains access to company resources.
3) Multi-Factor Authentication (MFA)
Companies need more sophisticated ways to prevent unauthorized access to mission-critical data and systems. Passwords are notoriously easy to crack. Hackers have tools that can find them, and users often forget to change default passwords or choose weak ones.
Today, multi-factor authentication (MFA) is the gold standard. MFA requires that 2 or 3 methods of authorization be used for access. Passwords can be combined with factors, such as a single use code, a personal question, or a biological marker. MFA is part of a zero-trust approach to security in which your company never trusts and always verifies.
4) Virtual Private Network (VPN)
Today’s remote workforce creates vulnerabilities when its members use Wi-Fi to access company applications and data. When working from outside the office, employees should use a virtual private network (VPN) to connect with the business network.
A VPN encrypts the connection from an endpoint, such as a mobile device, to a network, often over the Internet. Typically, a remote-access VPN uses IPsec or a Secure Sockets Layer to authenticate the communication between a device and the network.
5) Internal Risk
Employees can be both a liability and a first line of defense against cyberattacks. Staff members can accidentally delete information or fall for phishing scams by clicking on links in suspicious emails and activating ransomware.
Regular security awareness training can educate employees on how to recognize and avoid phishing attempts. Screening employees before hiring can prevent bad actors from gaining authorized access to your data and systems.
Finding the Right Security Tools
Once your company has assessed these areas of security, it’s time to start filling gaps. You’ll want to work with a technology partner that provides a wide range of leading security tools, allowing you to develop a comprehensive security strategy.
Citynet offers network, mobile device, and application security for SMBs in the West Virginia area. We have deep Cisco expertise and work closely with the Cisco team. Our Cisco certifications give our customers access to best-in-breed security tools along with the expertise to deploy and support them.
For example, Cisco AnyConnect can be used with MFA to create a secure connection between employee devices and your network. Citynet provides unified access security through Duo, which protects applications and mobile devices. We also partner with KnowBe4 to conduct security awareness training for employees.
Use Our Checklist
Does your company have a solid cyber security strategy? Use the Citynet Cyber Security Checklist to find out.