Personal pictures, social networking, online banking are all services that you should not do, or be logged in to on your work computer. Work computers are for work, visiting work-related…
Category: Security Tips

Don’t Invest in Social Media Hijacking
More than half of the world’s population uses at least one social media platform. Users can post to Facebook, Instagram, and Snapchat for all their followers to see. When a…
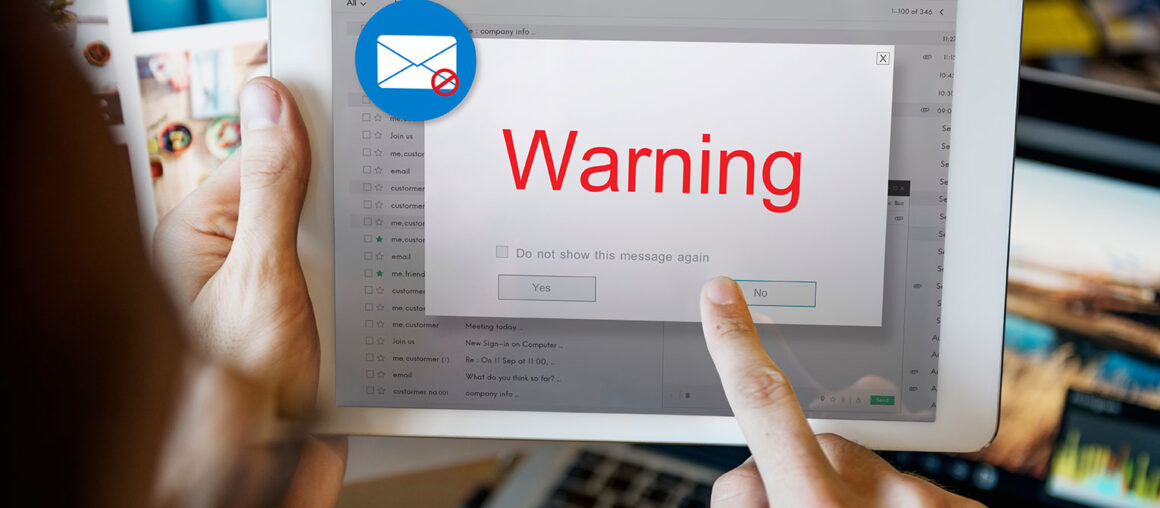
Social Engineering Red Flags #1: Sender
Cybercriminals send more phishing emails now than ever before. When you receive an email, it’s important to look for any red flags. One red flag you can look for is…

Lock Your Screen
Locking your screen when you leave your desk is a simple way to keep your information secure and is often overlooked. Keeping your screen unlocked can be dangerous for a…

URLs Are Only Half the Story
If you’ve taken security awareness training, you have probably been taught to hover your cursor over a link to view the destination URL. Checking the URL for things like misspellings,…

How to Be Prepared for Future Threats
New innovations in technology are being developed at a rapid rate. But new technology comes with new risks. Let’s go over some examples of how technology will change in the…

Booking a Vacation Rental? “Getaway” From These Scams
Getting ready for a vacation? If you plan to use a popular vacation rental website or application (app), such as AirBnB, HomeAway, or VRBO to find your next getaway, beware.…

The Role of Search Engine Optimization (SEO) in Cyberattacks
You probably use your favorite search engine, such as Google or Bing, to find more information about topics that interest you. Have you ever stopped to think about how the…

Who Is the True Target of Business Email Compromise (BEC)?
What is BEC? In a Business Email Compromise (BEC) attack, cybercriminals impersonate business professionals to trick victims into sharing information about their organization. This attack is an advanced form of…

Keeping Your Passwords Squeaky Clean
Did you know that the average person uses the same three to seven passwords to log in to over 170 online accounts? In addition to being reused, these passwords are…